AML risk assessment is essential for regulatory compliance and protection against financial crime. While not explicitly required by law, regulations such as the BSA, OFAC, and SRA mandate risk management programs to prevent money laundering, terrorist financing, and reputational damage. While it is difficult to remove all hazards, the goal is to minimize their impact. The heart of an effective AML risk assessment is a risk-based approach in which businesses customize their strategies to the specific dangers they face. The steps of an effective AML risk-based approach can be seen from below.
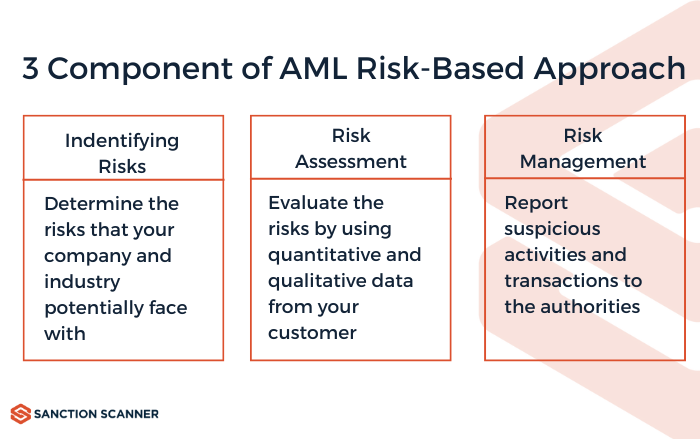
5 Steps of an Effective Risk Assessment
Potential harms threaten the company with financial and reputational consequences. Companies can lose money and reputation with their customers due to criminal activity. It is much easier to take precautions against these criminal activities than to deal with them after they happen. An effective AML risk assessment requires these 5 steps:
1. Identify the Risks
The first step in conducting an effective risk assessment is identifying the risks. This involves recognizing key risk indicators (KRIs) that could expose your organization to money laundering or terrorist financing. These factors include:
- Customer profiles
- Transactional behaviors
- Geographical regions
- The products or services offered
It’s essential to evaluate both inherent risks—those present without any mitigation—and residual risks, which remain after controls are applied. By identifying these risks in detail, you can lay the foundations for effective risk management and enable your organization to categorize these risks according to risk levels and types.
2. Quantify and Categorize the Risks
This step is divided into two parts:
- Quantification: This process involves estimating the probability and impact of each risk and giving a numerical value to assess its severity accurately.
- Categorizing Risks: This includes scoring factors based on their probability and impact. Most organizations use a scale of 1 to 3, with 1 being low risk and 3 being high risk. Large global money transfers, for example, may be rated 3 due to their high risk of abuse. However, controls like automatic transaction monitoring can help to reduce such high-risk scores.
In addition, a separate analysis of factors such as transaction volume, customer behavior, and geographic visibility is necessary to diversify the categorization. This structured approach allows businesses to prioritize risk areas and serves as a base for designing mitigation strategies.
3. Building a Risk Mitigation Strategy
After quantifying and categorizing risks, the next step is implementing a risk strategy to minimize potential risks. Here are the steps to create an effective AML risk model:
- Identify Key Risk Indicators (KRIs): Start by selecting the most critical risk indicators that impact your organization, such as customer types, transaction methods, or geographical locations.
- Assign Importance Levels: Assign a specific value to each risk factor based on its probability and the potential damage it can cause.
- Create a Scoring System: Develop a method for combining these risk factors to produce a total risk score. This can involve basic math like adding scores, using weighted averages, or more advanced calculations.
- Classify Risk Levels: Group the scores into categories (e.g., low, medium, high) to quickly identify which risks need more attention. This helps you properly prioritize different customer groups or transactions.
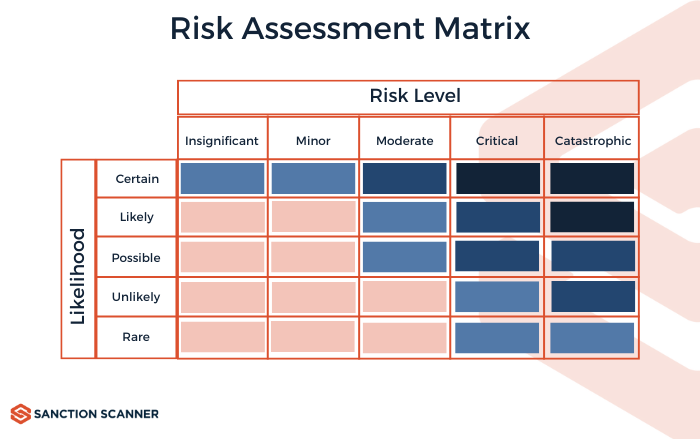
After these steps, an effective risk assessment matrix model should look like below example.
After establishing the risk model, solutions are also required to control and minimize your risks. This is the most important part of AML risk assessment. Here are some solutions for risk mitigation:
- Customer Due Diligence (CDD): For high-risk persons and companies, CDD includes comprehensive identity verification of the customers. For instance, customers who are categorized as politically exposed persons (PEPs) or who reside in high-risk jurisdictions might be asked to provide more documentation by financial institutions.
- Real-Time Transaction Monitoring: Advanced transaction monitoring systems can analyze your organization’s transactions as they occur, identifying patterns that indicate suspicious activity. These systems can also detect multiple small transactions that add up to a large amount, which is often indicative of structuring or smurfing.
- Suspicious Activity Reporting (SARs): Filing SARs promptly when you detect potentially suspicious behavior is critical to AML compliance and strengthens your organization’s cooperation with law enforcement to prevent potential risks.
By implementing these measures, organizations can strengthen their defenses against money laundering and financial crime while ensuring compliance with regulatory requirements. Regular reviews of these strategies will enhance their effectiveness over time.
4. Regular Review and Ongoing Adjustments
Once you have implemented risk controls, you must review your AML program and regularly react to changes. Some risks may be overlooked after controls are implemented, so ongoing evaluation is necessary to ensure appropriate mitigation. Key actions you need to consider are:
- Monitor Residual Risks: Regularly assess the effectiveness of your controls and make adjustments as risks evolve.
- Update Policies: Continuously revise your policies to align with regulatory updates and emerging threats.
- Conduct Audits: Regular audits highlight areas needing improvement and ensure the effectiveness of your controls.
- Adapt to Change: Risk assessments should evolve with new risks and business environments.
These adjustments are essential to maintaining a dynamic risk management strategy. The next step, Reporting, will ensure timely communication of suspicious activities to regulatory authorities.
5. Reporting
The final step in the risk assessment process is reporting, which combines all the previous steps and effectively communicates your findings. After identifying, categorizing, mitigating, and adjusting risks, financial institutions should carefully document the entire risk assessment process. This comprehensive report demonstrates that you comply with AML requirements and helps maintain transparency.
Inadequate and late reporting can negatively affect companies in terms of high penalties and reduced public credibility. So, ensure your findings and risk mitigation efforts are properly reported to regulators. A well-documented report also demonstrates your organization’s commitment to maintaining AML compliance.
How to Deal With Risk Assessment Procedure?
Risk management gets easier if a company applies a complete evaluation procedure. Once the potential and hazards are identified, officials can focus on high-risk customers and activities without wasting time with countless of them.
If the assessment process seems difficult, there is no need to worry about recent technological developments. Sanction Scanner provides software products for companies in financial services to evaluate their risks and then manage the whole operations accordingly.
Customer Risk Assessment Solution helps companies to;
- Easily set risk criteria and rules
- Determine customers’ risk levels according to your own indicators
- Have scorecards for each customer
- Manage alerts with different risk levels
Simplify Risk Assessment with a Sanction Scanner
Strengthen your business with greater control compliance with a risk-based approach and risk-based scorecard review. Sanction Scanner's AML risk assessment tools can help streamline and enhance your risk assessment process, allowing you to proactively identify and mitigate potential risks associated with money laundering and terrorist financing activities.



