What Is Fraud Prevention?
Fraud prevention aims to create strategies that best protect each industry, while considering the unique risks each sector possesses. Specifying fraud prevention measures to sectors like banking, fintech, crypto exchange, e-commerce, healthcare, telecommunication, and many more helps create a safer environment for each industry regardless of the complexity of their fraud struggles. In this blog post, we’ll be talking more about common trends of fraud in 2025, best tools and technologies to use for prevention, and more.
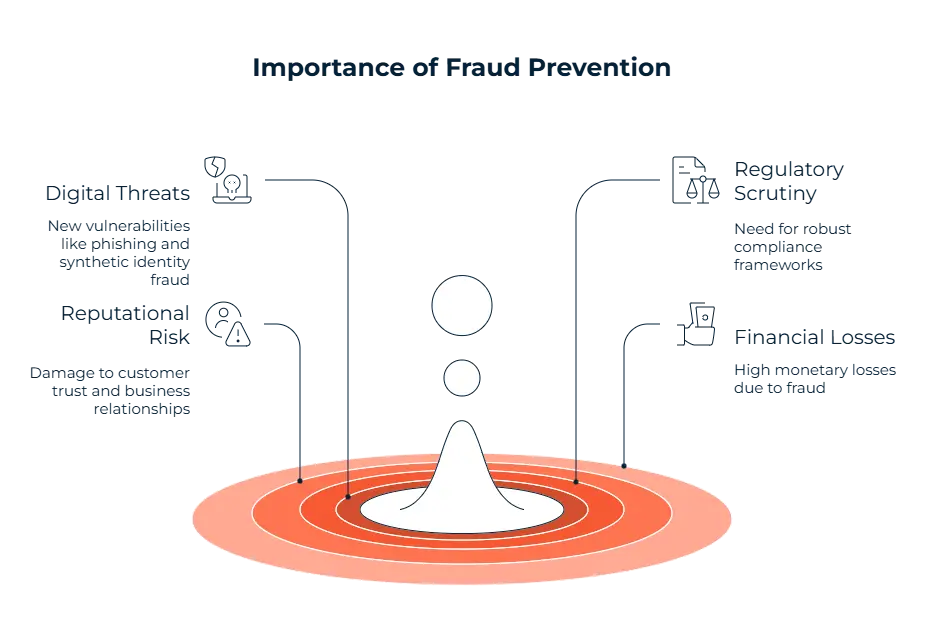
Why Fraud Prevention Important?
With technology developing and tools making it harder to detect fraud, having prevention tactics ready within your company is important. One of these threats that emerging technology brought forward is cybercrime. Techniques like deepfakes and synthetic identities are being used in the cryptocurrency space, and these make it harder to detect what’s real or fake. Another reason for your company to implement fraud prevention measures is the regulatory pressure that’s increasing each year. This pressure stems mainly from the General Data Protection Regulation (GDPR), payment standards like PCI DSS, and of course, anti money laundering (AML) requirements as a whole. Our Sanction Scanner experts say that consumers reported losing more than $12.5 billion to fraud in 2024, which represents a 25% increase over the prior year.
Reputation is also another problem you’ll face if your company is struggling with preventing financial crimes like fraud. One case of fraud can destroy the reputation and the relationship you’ve built with customers and investors. These cases of financial crime will surely lead to many consequences other than reputation damage. Financial fines is another consequence your company will suffer from. These fines can go up to millions, not counting the losses that the fraud itself will cause.
Common Trends of Fraud to Watch
Payment Fraud
There are several trends to watch out for if you’re looking to reach full AML compliance which will protect you against fraud and financial crime. The first risk that is still as prominent as ever is payment fraud. Credit card misuse, unauthorized transactions, and chargeback abuse is used to complete this type of fraud. Identity fraud is also used similarly by criminals, where they create synthetic IDs or use deepfakes to get through onboarding without getting detected.
Account Takeover
Account takeovers also cause great problems for companies and customers. This action is done by phishing attacks where login credentials get stolen. Once they get access, criminals lock real owners of the accounts out to then use the accounts for financial gain. According to the sources, account takeover (ATO) attacks increased 24% in Q2 2024 vs Q2 2023. Business email compromise (BEC) scams are also evolving along with technological developments. Fraudsters can now send fake invoices, deepfakes, and impersonate executives to trick employees into allowing wire transfers.
Insider Fraud
Insider fraud is another type that your company needs to be careful about. Embezzlement or misuse of access privileges of employees can be used for this fraud. In February 2025, the FCA secured a confiscation order of £586,711.01 against a former Goldman Sachs analyst Mohammed Zina convicted of insider fraud.
Loan and Insurance Fraud
The final type of fraud that continues to evolve is loan and insurance fraud. Fake applications and exaggerated claims drain resources from people that actually need it. For example, four individuals in Los Angeles were charged with insurance fraud after claiming that a bear had damaged their cars, when the bear in question was actually just a person dressed in a bear costume. The insurance companies were defrauded of $141,839, authorities say.
Fraud Prevention Checklist
For a strong fraud prevention system, there should be several steps to your solution.
Identity & Onboarding Controls
The first stage is conducting identity & onboarding controls. Tools like optical character recognition (OCR)-based document checks along with biometrics will help your company ensure that customers are who they claim to be. Sanctions and politically exposed persons (PEPs) checks later will give you an extra layer of protection by helping you figure out whether these customers are sanctioned or of high-risk.
Fuzzy Logic
Fuzzy logic usage helps you by detecting duplicates, which shows fraudsters that try to open several accounts with different name variations.
Transaction Monitoring
Another step to the system is behavioural and transaction monitoring. Real-time transaction monitoring is helpful for flagging suspicious activity when used with rule based alerts and risk scoring models. These risk levels created by the risk scoring models help you divide your monitoring attention proportionate to customers’ score. Especially for high-risk examples, manual review workflows are needed since they bring a professional’s approach to the more complex cases.
Authentication
One other step to create the perfect fraud prevention system is authentication and access security. After onboarding, more protection is needed for accounts to be safe to operate. Multi-factor Authentication (MFA) and role-based access management help you with cases of account takeover attempts and insider fraud. Other than this, anomaly detection based on IP, device, or login time is another effective protection layer that helps with prevention of fraud attempts. Internal risk controls within your company is another advice from our Sanction Scanner experts. Segregation of duties, regular financial reconciliation, and ongoing employee fraud awareness training is needed to reduce the risk of insider fraud.
Audit Trail
Another step to a strong fraud prevention system is reporting structrues as well as audit trails. Training staff to properly escalate fraud attempts using Suspicious Transaction Reports (STRs) and Suspicious Activity Reports (SARs) is needed. Additionally, maintaining audit-ready documentation and establishing an escalation system with appropriate teams is helpful for full compliance.
Post Incident Response
The final advice for the perfect system to have is its ability to create the appropriate post-incident response. Your company should be testing your incident response plans and conducting root cause analyses to strengthen defense. In the case of an incident, you should be ready to notify and support affected users without losing no time.
Best Practices for Fraud Prevention in 2025
Let’s talk more about the updates your already existing fraud prevention system might need. You should be strengthening your company’s KYC efforts with newer technology like biometrics and video verification. Risk based monitoring and AI-powered real-time anomaly detection is there to help you identify suspicious activity immediately, so that your company can alert the activity quickly. MFA is also another layer of security for your system, and adding regular awareness training on subjects like phishing and social engineering will help your employees avoid fraud further. A clear response plan for fraud cases is also essential.
Leading Tools and Technologies for Fraud Detection
There are many tools and technologies you can use to ensure prevention of fraud within your company. Transaction monitoring systems like Sanction Scanner are known for featuring both rule-based and behavioural analysis. These systems help detect odd activity immediately. Another category is identity verification tools. Tools that allows biometrics and liveness checks like Onfido and IDenfy help figure out whether the customer is who they claim to be. Device behavioural analysis is done by fingerprinting and inspecting mouse or key patterns. Sanctions screening is done by using PEP and blacklist checks, which helps prevent the entry of sanctioned individuals as well as keeping an eye on high-risk ones. Machine learning models also contribute by analysing large datasets to identify anomalies that might lead to or indicate fraud.
The U.S. Department of the Treasury announced that it enhanced its fraud detection and prevention mechanisms, including machine learning and AI tools. As a result, in FY 2024 it prevented or recovered over $4 billion in fraud and improper payments, up from $652.7 million in FY23.
| Tool Type | Examples / Features |
| Transaction Monitoring | Rule-based + behavioral analytics (e.g., Sanction Scanner) |
| Identity Verification | Biometrics, liveness detection |
| Device Behavioral Analysis | Device fingerprinting, keystroke patterns |
| Sanctions and Blacklist Screening | Screen against sanctions, PEPs, |
| Machine Learning Models | Real-time anomaly detection |
Fraud Prevention in Different Industries
Fraud prevention strategies differ from industry to industry. In banking and fintech, AML/KYC efforts are taken seriously since they heavily deal with money. Transaction scoring is used to help these companies better detect suspicious activity. E-commerce companies suffer mostly from chargeback fraud. In order to fight this, they use fraud scoring systems to flag risky orders. In another industry, healthcare, companies combat fraud by using claim monitoring. Fraudulent submissions can be detected and financial losses can be reduced accordingly thanks to monitoring efforts. Telecom companies deal with fraud mostly by preventing SIM swapping, which is a type of account takeover fraud where criminals transfer a phone number to a different SIM card to then use for fraudulent activity. Finally, crypto and Web3 space uses wallet screening and secures digital assets against unathorized access.
FAQ's Blog Post
Implementing multi-factor authentication, employee training, and real-time monitoring are among the most effective fraud prevention strategies. These reduce both internal and external threats.
Businesses can detect fraud early by using AI-powered analytics and setting up automated alerts for suspicious transactions. Early detection minimizes financial loss and reputational damage.
Well-trained employees are better equipped to recognize phishing, social engineering, and internal fraud risks. Regular training builds a culture of compliance and awareness.
Fraud prevention tools analyze patterns, flag anomalies, and block high-risk activities in real-time. They use machine learning to improve accuracy over time.
Data encryption secures sensitive information during storage and transfer, preventing unauthorized access. It’s a core component of cybersecurity and fraud prevention.
Yes, many fraud prevention tools offer scalable pricing for small businesses. Simple steps like employee awareness and basic software can significantly reduce risk.
Fraud risk assessments should be performed at least annually or whenever major business changes occur. Frequent reviews help update controls and detect new vulnerabilities.
Unusual spending patterns, duplicate payments, and login attempts from unknown locations are common signs. Monitoring these indicators is key to preventing fraud.